Articles sources : http://www.ehow.com/how_2171609_prevent-website-hackers.html?ref=fuel&utm_source=yahoo&utm_medium=ssp&utm_campaign=yssp_art
Followers
Monday, January 19, 2009
Prevent from hackers
Articles sources : http://www.ehow.com/how_2171609_prevent-website-hackers.html?ref=fuel&utm_source=yahoo&utm_medium=ssp&utm_campaign=yssp_art
Prevent from hackers
Articles sources : http://www.ehow.com/how_2171609_prevent-website-hackers.html?ref=fuel&utm_source=yahoo&utm_medium=ssp&utm_campaign=yssp_art
Saturday, January 17, 2009
What is Network

A group of two or more computer systems linked together. There are many types of computer networks, including:
In addition to these types, the following characteristics are also used to categorize different types of networks:
Computers on a network are sometimes called nodes. Computers and devices that allocate resources for a network are called servers.
(v.) To connect two or more computers together with the ability to communicate with each other.
Articles source : http://www.webopedia.com/TERM/N/network.html
Friday, January 16, 2009
Comparison linux and windows
Most standard computer programs are available for Linux. If you depend on specialized programs, such as specific genealogy programs, you will need to run Windows; more about this at the end.
Several Linux programs can read and write Microsoft Office files. So, if all you do with a computer is manage e-mail, create documents, create graphics files and use spreadsheets, Linux programs do all those things very well.
Until recently Linux has been more difficult to install and use than Windows. However, over the last two years there has been a concerted effort by several Linux companies to make Linux easy to use by an average user.
But why should one bother learning to use a new operating system other than the Windows one she is now using?
Here are the reasons:
- Linux hardly ever crashes, mainly because the basic low-level operating program (called the kernel) that keeps the computer running is small. So, even when things go wrong with some higher-level part of the operating system or with a program, the kernel keeps chugging away.
- Linux almost never has to be rebooted after installing a new program. This saves much valuable user time and aggravation over the life time of a machine.
- In most cases the Linux file system does not have to be defragmented regularly, such as Windows does, to keep it from slowing down.
- Linux allows up to 16 different views of the desktop, I use 4 of them. In other words, programs that are running can be associated with different views of the desktop; you will see only the program windows for the desktop view of current interest. It is easy to switch from one desktop view to another by buttons on the task bar.
- There are many free or inexpensive programs available for Linux.
- It cost less to install and operate.
By the way, most of the servers that provide web pages on the Internet are running Linux.
There are several different versions of Linux that are vying now for the desktop market. I have tried Red Hat and Linspire (previously called Lindows, a version of Debian). I highly recommend LinSpire (http://www.linspire.com) for general users for the following reasons:
- It is inexpensive.
- It is designed to look and operate very much like MS Windows.
- It installs easily and fast.
- It comes loaded with all the programs that are needed for web browsing, e-mail, and word processing and many other tasks.
- It has good on-line support.
- It has an inexpensive add-on called Click-N-Run that allows the user to simply click on hundreds of programs toLinspire install them on Linspire. (Buy Linspire and Click-N-Run together to save money.)
- Permission is not needed from Microsoft or Linspire.com to move Linspire from one machine to another owned by the same person. In fact, it can be installed on as many computers as there are in a given home at no extra charge.
- You can install it as a dual boot with a Windows system in order to try it out while still keeping Windows available.
- You can get Linspire on an inexpensive light-weight notebook.
If there is a need for a few specialized programs that are not available for Linux, one can run Win4Lin in Linspire in order to be able to run Windows 98 (Win4Lin Version 9x) or Windows XP (Version Pro 1.1). the total cost for both Win4Lin and Windows 98 is about $200. I have done this on my Linspire notebook and it works very well. You can buy Win4Lin 9x on Click-N-Run.
One last note: Linspire does not automatically set up a non-root account. It is best to do that and always run programs from that account. Then only use the root account when changes need to be made to the system that only a root account is allowed to do.
For information about how I set up a Linspire light-weight notebook to run Windows 98: http://www.roperld.com/GenLinNotebook.htm
Articles source : http://arts.bev.net/roperldavid/Linwincomp.htm
Thursday, January 15, 2009
What is CPU
On large machines, CPUs require one or more printed circuit boards. On personal computers and small workstations, the CPU is housed in a single chip called a microprocessor. Since the 1970's the microprocessor class of CPUs has almost completely overtaken all other CPU implementations.
The CPU itself is an internal component of the computer. Modern CPUs are small and square and contain multiple metallic connectors or pins on the underside. The CPU is inserted directly into a CPU socket, pin side down, on the motherboard. Each motherboard will support only a specific type or range of CPU so you must check the motherboard manufacturer's specifications before attempting to replace or upgrade a CPU. Modern CPUs also have an attached heat sink and small fan that go directly on top of the CPU to help dissipate heat.
Two typical components of a CPU are the following:
- The arithmetic logic unit (ALU), which performs arithmetic and logical operations.
- The control unit (CU), which extracts instructions from memory and decodes and executes them, calling on the ALU when necessary.
Tuesday, January 13, 2009
How to Choose the Right Webcam For You
A webcam is a camera which is directly connected to a PC and, in many cases, the internet. A webcam is also almost always able to record video, not just still frames (though many can capture both). The objective is to record video directly onto your PC's hard drive, rather than onto a tape or onto the hard drive of an external camera.
Sometimes, people don't use Webcams to record video at all, opting instead to send live video "streaming" across the internet to a website or another computer's monitor.
Important Specifications for Webcams
There aren't a whole lot of technical details for webcams to differ from model to model. Here are a couple of the big ones you should keep in mind:
- Resolution–The size and, ultimately, quality and clarity of the video you'll be recording. Larger numbers are better, but also use more hard drive space.
- Frame Rate–The speed at which your video will be recorded in Frames Per Second, or FPS. This can mean the difference between a choppy set of still images (10 fps) to a smooth, cinema-like flow of sharp video (30 or 60 fps).
How do you choose the best webcam?
Your options for buying a webcam will be largely dependent upon what you want to do with it. People use webcams for all kinds of purposes, including to have video chats, to hold online business meetings or teleconferences, to monitor a situation or location from great distances, or to record and upload video diaries (aka video blogs, or "vlogs") to YouTube or their personal website.
If you plan on mainly video chatting with friends, or uploading video diaries to YouTube, the most simplistic of cameras will serve you just as well as the more expensive brands. These less expensive models will generally have a standard resolution of (640x480)–that's about as low as you should be going when it comes to resolution these days. These cameras will run well less than $100 from any retailer.
More exciting, and a little more expensive (though not as much as you'd think), you can actually buy webcams that record in High Definition resolution (960x720 or greater). These models cost closer to $100 on average, though still not much more than that.
Alternative Solutions
There are a couple of other options consumers have when it comes to more specialized webcam functions. In many cases, a standard video camera that can be found in many households today can be connected to a computer and utilized as a live webcam. This is an interesting option for people looking to have more control over their camera, and who need to utilize features such as zoom, tripod placement, or even multiple cameras simultaneously.
Of course, the more complicated the application, the more software and equipment are needed. But for most users, a simple webcam is a smart, fun way to become even more connected to the world around you.
Articles source :http://peripherals.about.com/od/webcamerasvideoinputs/a/BYBWebcam.htm
Monday, January 12, 2009
Assemble PC


How To Assemble A Desktop PC
Components Procedure
Power Supply (PSU)
Install the power supply into the pc casing. Use the Philips screw driver to put screw for the PSU.

Motherboard
Install the system board.
Connect the system unit with front panel switches and the indicators to the system board. Verify system board jumper & switch setting.
Processor
Install the processor the PGA socket on the motherboard. Beware when pin0in the processor heatsink.
RAM
Install the memory module to the memory slot on motherboard.
Hard Disk
Install hard disk into pc case. Then, connect it with data cable (IDE,SATA) to the motherboard. Connect the hard disk with power cable (molex) from PSU.
Optical Drive
Install the optical drive (DVD Drive or CD Drive) into the pc casing. Then, connect it with data cable (IDE, SATA). Connect it with power cable (molex) from PSU.
Video Card/Graphics Card/GPU
Install the display adapter into the graphics slot (AGP, PCI-E). Then connect the graphics card with the power cable if it need extra power(graphics card requirement)
Keyboard
Connect the keyboard to the PS/2 port at back-side panel of casing.
Mouse
Connect the keyboard to the PS/2 port at back-side panel of casing.
Monitor
Connect the VGA cable from monitor to the graphics card. Then plug the monitor to electric.
Basic tools
Before you begin building or refitting a computer, you will need some basic tools:
1. 2 phillips-head (cross-shaped) screwdriver
2. Needlenose pliers
3. Anti-static Wrist Strap
4. A large level working space
What is RAM?
Types of RAMs
The most widely used RAMs today are SRAMs (static RAMs), which stores data in a state of a flip-flop, or DRAMs (dynamic RAMs), Flash, and EPROM, which stores data as a charge in a capacitor. Another well known type of RAM, a ROM, is a type of a RAM that has permanently enabled/disabled selected transistors by using a metal mask. ROMs thus cannot store any further charges.
Flash memory is also widely used. Because SRAMs and DRAMs are known to be highly volatile, many new products adopt the flash memory technology. Some examples of devices using flash memory include portable music players, scientific calculators, mobile phones, and even certain types of personal computers such as the One Laptop per Child (OLPC) devices. Flash memory is divided into two types: the NOR type and the NAND type. The NOR type is the one able to conduct a random access, therefore being widely used as a ROM in today's market. However, as the NOR is not able to, it is often used in flash USB drives.
In today's computers, RAMs are shipped in a form of module known as DRAM modules or memory modules. It is about the size of a chewing gum and with the Plug n Play technology, these can easily be replaced by taking it out of the port and replacing it with a new one. Not to forget, there is also an extremely small amount of RAM (known as SRAMs) within CPUs, motherboards, hard drives, and other parts of the system.
RAM Swapping
Sometimes people will need more memory than what the RAM installed can offer during intensive application cycles. During these sessions, the computer will conduct a task known as swapping. This is when the computer temporarily uses the hard drive space in place of the memory. Thrashing is the term for constantly swapping, but as the name's connotation suggest, constant thrashing can decrease the overall system performance. More RAM being added can reduce the swapping rate.
Security Concerns
SDRAMs are known to not fully shut off when the power is cut. Instead, the stored memory is faded away. While this fading away only takes seconds in a normal room temperature, which is not the case in lower temperatures, which then the fading away can take up to minutes. Therefore, encrypted information could potentially be leaked as it is still stored in the memory.
Recent Developments
Currently non-volatile RAMs are under development, which will mean that memory can still be stored when the power is shut off. The more advanced step yet to have been taken was in 2004 when Nantero developed a fully functioning carbon nanotube memory type holding 10 GB. Recently in 2006, "Solid State Drives" with sizes of 150 GB and a faster speed than the normal hard drives have been created.
Artical from : http://www.tech-faq.com/ram.shtml
Introduction to computer
A computer system has three main components which is hardware, software and people
Hardware
The computer itself-and its associated equipment.
Software
The instructions that tell computer what to do. Software is also referred to as programs. More specifically, a program is a set of step-by-step that direct computer to do the task wanted and produces desire results.
People
A computer programmer is a person who write programs. Most of us simply use computer software written by someone else. This means were are users or people who purchase and computer software.
Computer is a machine that accepts data(input) and process it into useful information(output). A computer system consists of four main areas of data of handling which is input, processing, output and storage.
Sunday, January 11, 2009
Internet security
Today's Web is vastly different from yesteryear's Web and today's malware is vastly different from yesteryear's virus. No longer a form of digital graffiti, modern day malware is all about money. Your money, that is. This change in intent has also led to a corresponding change in tactics. Modern day malware is made to hide. Social engineering scams are increasingly sophisticated. Man-in-the-middle attacks can forcibly redirect you to hostile websites.
The Web has also changed. No longer a static one-sided delivery method, today's websites host and push content from a variety of sources. And the notion of surfing to only "known good sites" no longer applies. Today's dynamic Web technologies lend themselves to mass compromise of perfectly legitimate websites, outfitted with malicious scripts that turn the "known good site" into a virtual conveyor belt of malware.
The same technologies that foster Web developments also enable attackers to work smarter and faster. An attacker can use virtual hosting providers that redirect (and mask) a site's true origin. Automated tools leverage search engines to ferret out sites vulnerable to compromise. Other automated tools allow attackers to continually churn out repackaged malware designed to thwart signature-based antivirus. And in the darkest recesses of the Internet, the attackers use blogs, forums, and chat to barter malware and exploit frameworks.
And all of this is designed for profit - tricking you into laundering money, stealing your credit card details, siphoning your bank accounts, and even outright identity theft. Don't look to your bank to protect you either - if you don't directly foot the bill for the stolen funds, you'll indirectly pay for it with higher fees and higher prices sometime down the road.
The threat of compromised websites
Web pages are coded in various browser-friendly scripting languages, typically including combinations of HTML, Javascript, ActiveX, and CSS. When a request to a website is made, the source code for that page is loaded and interpreted by the browser. What you see in your browser is the visual manifestation of the source commands.
A Web page isn't just static content from one source. It supports multiple types of active content, including from third-parties. Google Adsense is a good example of that (as is any other third-party advertising included on a site). The same programming techniques used to load third party advertising can be used to load any third party content, including malicious content if so desired. And attackers use that to their advantage.
In other words, when you visit one website, you are in reality pulling content from several different sites and servers. In the past, the biggest web risk was that third party content might be booby-trapped. For example, a rogue advertiser might insert a malicious banner ad into the advertising network, which then was pulled by all participating websites.
Today, the risk has shifted dramatically. Attackers are directly compromising websites and outfitting them with malicious external calls to hostile content.
SQL Injection Attacks
One of the most common forms of Web site compromise are via SQL injection compromise. SQL is short for Standard Query Language, a scripting language used to manage databases. Many/most websites use some sort of database backend. This can be for everything from creating all or most of the site pages to storing information and generating search results pages. SQL injection attacks are malformed SQL queries that instruct the database to take some sort of unintended action beyond just returning requested data. In other words, a SQL injection attack tricks the database into responding to the query as if it were a command to take some specific action, versus just returning some type of information.
A database that is vulnerable to SQL injection can be compromised in a number of ways. Of most concern from an Internet safety standpoint are SQL injection attacks that embed malicious hidden iframes and malicious external references within the source code of the compromised Web pages.
When a Web surfer encounters one of these compromised pages, these hostile third-party references call up exploit code and malware from the attacker-owned sites. This action is invisible to the Web surfer - only a thorough examination of the website source code provides the tell-tale signs of the compromise; the page displayed by the browser looks perfectly normal.
Beginning in late October 2007, a series of SQL injection attacks began which continue to compromise millions of Web pages (past compromises include Ikea and WalMart). And because the malware is being delivered from reputable (but compromised) websites, the old advice to only surf to known reputable sites no longer helps. Worse, the malware foisted by the compromised sites typically consists of password stealers and backdoors. These password stealers and backdoors can be used to steal credit card information, bank account login credentials, and other sensitive financial or personal information.
When encountering one of these compromised sites, chances are you won't notice anything awry. The malware launches silently and once on the system it often uses rootkit technology to hide itself.
Staying Safe Online
Internet safety isn't about avoiding the unknown or untrusted. Today, Internet safety also includes guarding against threats coming from even the most staid, legitimate, and otherwise honorable websites. Or in the words of the X-Files, 'trust no one'.
To avoid being victimized by a compromised website, either use the NoScript addon for Firefox, or disable active scripting in Internet Explorer and Opera. For further details, see Web Browser Security. In addition, follow these computer safety tips to lessen your susceptibility should exposure occur.
article souce : http://antivirus.about.com/od/securitytips/a/internetsafety.htm
Saturday, January 10, 2009
Spyware/adware
Spyware is software that has been created to track and report what you do on the computer! Some of the "worst" spyware will actually search your hard drive for personal information, credit card numbers, bank accounts, passwords, and other confidential information. Adware or Adaware is software that turns your computer into a "billboard" constantly loading ads onto your screen.
Wednesday, January 7, 2009
To manually install Windows Backup
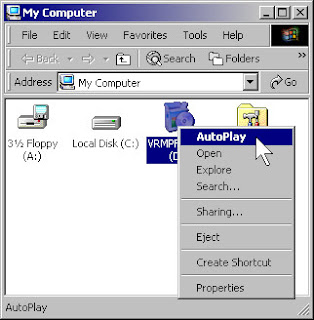
1.Insert your Windows XP CD into your CD drive. If Windows XP Setup does not appear after several seconds, open My Computer, right-click your CD drive, and then click AutoPlay.
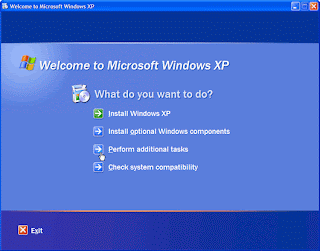
2.In the Welcome to Microsoft Windows XP window, click Perform additional tasks.
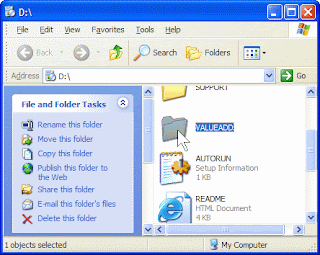
3.Click Browse this CD.

4.Double-click VALUEADD, double-click MSFT, and then double-click NTBACKUP to open the \VALUEADD\MSFT\NTBACKUP folder.
5.In the NTBACKUP folder, double-click NTBACKUP.
6.After setup is complete, click Finish.

You can now start Windows Backup by clicking Start, pointing to All Programs, pointing to Accessories, pointing to System Tools, and then clicking Backup. For more information about protecting your files from computer failure, read Back up your files.
Articles source : http://www.microsoft.com/windowsxp/using/setup/maintain/backupsw.mspx
Create a folder structure
•Finances: Documents related to your budget and taxes
•School: Class notes and reports
•Work: Your résumé and other work-related documents
•Shopping: Notes comparing different products and stores
•Home: Records relating to home maintenance and improvements
To create a folder structure
1.Click Start, and then click My Documents.
2.Click the File menu, click New, and then click Folder.
3.Type the name for your new folder, and then press ENTER.
My Documents window with new folder
4.Repeat steps 2 and 3 to create additional folders.
Note: You can create sub-folders within folders for multiple levels of organization.
After you have created your folder structure, you can move files into your new folders
1.In My Documents, select the files or folders that you want to move. To select multiple files, hold down the CTRL key and click each file you want to select.
2.Click the Edit menu, and then click Cut.
My Documents Edit menu with Cut selected
3.Open the folder you want to store your files in. Click the Edit menu, and then click Paste.
Edit menu with Paste selected
4.Repeat steps 1-3 until you have moved all of your files to their new locations.
Now that you have an organized system of folders, when you save new files, be sure to save them in one of your folders to keep things organized.
Top of pageTop of page
Browsing files
Sometimes you know where a file is stored, but there are so many files in the folder that it's difficult to find the file you want. The best way to search through a large folder is to use the Details view. The Details view allows you to quickly sort your files and view different types of information about all the files in a folder.
To use the Details view
1.Open the folder you want to browse
2.Click the Views button, and then click Details.
Folder with Details selected from expanded list of view options
3.To sort the files, click the column heading that you want to sort by. For example, to sort files from oldest to newest, click the Date Modified heading. To reverse the sort order (for example, to sort from newest to oldest), click the column heading twice.
Folder with images sorted by date modified
4.By default, the Details view shows the file name, date, size, and type. You can add other information as well. To add or remove columns, right-click a column heading, and then click More.
Adding detail information for images in a folder
5.In the Choose Details dialog box, select the columns you want to see in the Details view. For pictures and videos, you can add Dimensions to sort by size. For music, you can add Artist, Album Title, and Genre to make it easier to find the songs you want.
Choose Details dialog box
6.Click OK to add the columns to your Details view.
Choose Details window with OK button selected
When you modify the columns in the Details view, it affects only the folder you are viewing. To change the layout of all folders on your computer, read Specify how folders open.
Top of pageTop of page
Searching for files
If you don't remember which folder you saved a file in, you can search for it. To search for a file
1.Click Start, and then click Search.
Start menu with Search selected
2.In the left pane, click the type of file you want to search for, or click All files and folders.
Search pane
3.Based on the type of file you chose to search for, specify your criteria. If you know part of the file name, type it. Then click Search.
Search pane with file type selected and file name text typed in text box
4.Windows XP searches your computer, which may take several minutes. Windows XP then displays the search results, which you can browse just like files in a folder. Once you are done searching, click Yes, finished searching.
Tip
Tip: If you want to view any of the search results, double-click the file and it will open in the relevant application. You can do this as many times as necessary to find the file you need.
Search pane, with Search results
Note: For even faster search results, download and install the MSN Search Toolbar with Windows Desktop Search. With Windows Desktop Search, you can find files on your computer in just a few seconds.
Articles source : http://www.microsoft.com/windowsxp/using/setup/maintain/filemgmt.mspx
Best Practices for Maintaining Your Computer
2.Install only licensed programs. Make sure you or your company has a license for any software you install on your work computer. Your company can get sued for having software without a license installed on its machines. For example, installing a program your friend bought could present some problems. Software that you've bought a license for is probably fine, but double-check the license to make sure. Sometimes, software licenses bought for home use can not be installed at work as well.
3.Don't install different versions of software. Even if you prefer the version of software you use at home rather than work, don't install it on your work computer. You could have incompatibility problems with co-workers and your specific line of business applications. Your IT department may also not be able to make any required updates or provide technical support.
4.Let IT know when hardware isn't working. Fixing a broken computer yourself could just cause more problems. Your fixes, for example, could make the computer incompatible with the corporate network. Most IT departments have a helpdesk or technical assistance program designed for this type of work. The IT department may have already seen the same problem and have a known fix. Helping your IT department track common computer problems can also help them decide which brand and make of computer to order in the future.
5.Let IT know when you need something. Giving the IT department reasonable requests and adequate time for planning can help them respond to your needs. Otherwise, you may end up with computer software or hardware you didn't want—which can hinder how effective you are at work.
6.Don't download programs from Internet sites you don't trust. By downloading programs that may not be secure, you put all the computers on the network at risk.
7.Be aware of suspicious e-mails. Viruses introduced though e-mail may be disguised as a downloadable file. If an e-mail you receive is from someone you don't know, has strange text, or otherwise looks suspicious, contact your IT department. If you open it, you could potentially cause problems for you and you co-workers. If it is a virus, the IT department can ask other employees in the organization to look for similar e-mails.
8.Use online support resources. Many IT departments have created online internal help sites that could provide an answer to your computer problem. Each day, Help desks typically receive many questions that are already answered at these sites. The Gartner Group, which provides research and analysis on the IT industry, predicts that by 2005 support calls will be cut in half. Instead, employees will use self-help options—such as frequently asked questions (FAQ) and online how-to guides—to help solve problems. For help effectively using Microsoft products, you can also use the following resources:
•Microsoft Office Online Assistance Center
•Microsoft Knowledge Base
•Microsoft Windows XP Support Center
Articles source : http://www.microsoft.com/atwork/getstarted/maintain.mspx
keyboard
TYPES OF KEYBOARDS
QWERTY Keyboard - Developed by Sholes in 1868 and is now the official standard of computer keyboards [ISO9995]. The layout of the QWERTY keyboard was designed for two finger typing and was designed to help prevent stuck keys. Now with new technology, stuck keys are no longer an issue; and with the position of the keys, the hands are held close together helping to cause Carpal Tunnel Syndrome. Given all the above problems, this is the most widely used keyboard because the lack of options, can be used without training, is used because of the difficulty of having to teach a different keyboard, and is cheap and easy to find.
Dvorak Keyboard - Developed by Dr. August Dvorak in 1936 as a solution to the outdated QWERTY keyboard. The layout of the keys on this keyboard make it easier and faster to type on when compared with other keyboards.
Chiclet Keyboard - Very small keyboard that was introduced with the PC Jr. with small keys spread out.
KEYBOARD LAYOUTS
Below is a few of the keyboard layouts explained in the above section.


information about graphic card
The images you see on your monitor are made of tiny dots called pixels. At most common resolution settings, a screen displays over a million pixels, and the computer has to decide what to do with every one in order to create an image. To do this, it needs a translator -- something to take binary data from the CPU and turn it into a picture you can see. Unless a computer has graphics capability built into the motherboard, that translation takes place on the graphics card.
A graphics card's job is complex, but its principles and components are easy to understand. In this article, we will look at the basic parts of a video card and what they do. We'll also examine the factors that work together to make a fast, efficient graphics card.

2008 HowStuffWorks
The graphics card creates a wire frame image, then fills it in and adds textures and shading.
Think of a computer as a company with its own art department. When people in the company want a piece of artwork, they send a request to the art department. The art department decides how to create the image and then puts it on paper. The end result is that someone's idea becomes an actual, viewable picture.
A graphics card works along the same principles. The CPU, working in conjunction with software applications, sends information about the image to the graphics card. The graphics card decides how to use the pixels on the screen to create the image. It then sends that information to the monitor through a cable.
The Evolution of Graphics Cards Graphics cards have come a long way since IBM introduced the first one in 1981. Called a Monochrome Display Adapter (MDA), the card provided text-only displays of green or white text on a black screen. Now, the minimum standard for new video cards is Video Graphics Array (VGA), which allows 256 colors. With high-performance standards like Quantum Extended Graphics Array (QXGA), video cards can display millions of colors at resolutions of up to 2040 x 1536 pixels. |
Creating an image out of binary data is a demanding process. To make a 3-D image, the graphics card first creates a wire frame out of straight lines. Then, it rasterizes the image (fills in the remaining pixels). It also adds lighting, texture and color. For fast-paced games, the computer has to go through this process about sixty times per second. Without a graphics card to perform the necessary calculations, the workload would be too much for the computer to handle.
The graphics card accomplishes this task using four main components:
- A motherboard connection for data and power
- A processor to decide what to do with each pixel on the screen
- Memory to hold information about each pixel and to temporarily store completed pictures
- A monitor connection so you can see the final result
Processor and Memory

2008 HowStuffWorks
Graphics cards take data from the CPU and turn it into pictures. Find out the parts of a graphics card and read expert reviews of graphics cards.
Like a motherboard, a graphics card is a printed circuit board that houses a processor and RAM. It also has an input/output system (BIOS) chip, which stores the card's settings and performs diagnostics on the memory, input and output at startup. A graphics card's processor, called a graphics processing unit (GPU), is similar to a computer's CPU. A GPU, however, is designed specifically for performing the complex mathematical and geometric calculations that are necessary for graphics rendering. Some of the fastest GPUs have more transistors than the average CPU. A GPU produces a lot of heat, so it is usually located under a heat sink or a fan.
In addition to its processing power, a GPU uses special programming to help it analyze and use data. ATI and nVidia produce the vast majority of GPUs on the market, and both companies have developed their own enhancements for GPU performance. To improve image quality, the processors use:
- Full scene anti aliasing (FSAA), which smoothes the edges of 3-D objects
- Anisotropic filtering (AF), which makes images look crisper
Each company has also developed specific techniques to help the GPU apply colors, shading, textures and patterns.
As the GPU creates images, it needs somewhere to hold information and completed pictures. It uses the card's RAM for this purpose, storing data about each pixel, its color and its location on the screen. Part of the RAM can also act as a frame buffer, meaning that it holds completed images until it is time to display them. Typically, video RAM operates at very high speeds and is dual ported, meaning that the system can read from it and write to it at the same time.
Integrated Graphics Many motherboards have integrated graphics capabilities and function without a separate graphics card. These motherboards handle 2-D images easily, so they are ideal for productivity and Internet applications. Plugging a separate graphics card into one of these motherboards overrides the onboard graphics functions. |
The RAM connects directly to the digital-to-analog converter, called the DAC. This converter, also called the RAMDAC, translates the image into an analog signal that the monitor can use. Some cards have multiple RAMDACs, which can improve performance and support more than one monitor. You can learn more about this process in How Analog and Digital Recording Works.
The RAMDAC sends the final picture to the monitor through a cable. We'll look at this connection and other interfaces in the next section.
Input and Output
Graphics cards connect to the computer through the motherboard. The motherboard supplies power to the card and lets it communicate with the CPU. Newer graphics cards often require more power than the motherboard can provide, so they also have a direct connection to the computer's power supply.
Connections to the motherboard are usually through one of three interfaces:
- Peripheral component interconnect (PCI)
- Advanced graphics port (AGP)
- PCI Express (PCIe)
Most graphics cards have two monitor connections. Often, one is a DVI connector, which supports LCD screens, and the other is a VGA connector, which supports CRT screens. Some graphics cards have two DVI connectors instead. But that doesn't rule out using a CRT screen; CRT screens can connect to DVI ports through an adapter.
Most people use only one of their two monitor connections. People who need to use two monitors can purchase a graphics card with dual head capability, which splits the display between the two screens. A computer with two dual head, PCIe-enabled video cards could theoretically support four monitors.
 Photo courtesy of HowStuffWorks Shopper This Radeon X800XL graphics card has DVI, VGA and ViVo connections. |
In addition to connections for the motherboard and monitor, some graphics cards have connections for:
- TV display: TV-out or S-video
- Analog video cameras: ViVo or video in/video out
- Digital cameras: FireWire or USB
| APIs are different from drivers, which are programs that allow hardware to communicate with a computer's operating system. But as with updated APIs, updated device drivers can help programs run correctly. |
Choosing a Good Graphics Card
A top-of-the-line graphics card is easy to spot. It has lots of memory and a fast processor. Often, it's also more visually appealing than anything else that's intended to go inside a computer's case. Lots of high-performance video cards are illustrated or have decorative fans or heat sinks.But a high-end card provides more power than most people really need. People who use their computers primarily for e-mail, word processing or Web surfing can find all the necessary graphics support on a motherboard with integrated graphics. A mid-range card is sufficient for most casual gamers. People who need the power of a high-end card include gaming enthusiasts and people who do lots of 3-D graphic work.
 Photo courtesy of HowStuffWorks Shopper Some cards, like the ATI All-in-Wonder, include connections for televisions and video as well as a TV tuner. |
A good overall measurement of a card's performance is its frame rate, measured in frames per second (FPS). The frame rate describes how many complete images the card can display per second. The human eye can process about 25 frames every second, but fast-action games require a frame rate of at least 60 FPS to provide smooth animation and scrolling. Components of the frame rate are:
- Triangles or vertices per second: 3-D images are made of triangles, or polygons. This measurement describes how quickly the GPU can calculate the whole polygon or the vertices that define it. In general, it describes how quickly the card builds a wire frame image.
- Pixel fill rate: This measurement describes how many pixels the GPU can process in a second, which translates to how quickly it can rasterize the image.
Overclocking Some people choose to improve their graphics card's performance by manually setting their clock speed to a higher rate, known as overclockings. People usually overclock their memory, since overclocking the GPU can lead to overheating. While overclocking can lead to better performance, it also voids the manufacturer's warranty. |
The graphics card's hardware directly affects its speed. These are the hardware specifications that most affect the card's speed and the units in which they are measured:
- GPU clock speed (MHz)
- Size of the memory bus (bits)
- Amount of available memory (MB)
- Memory clock rate (MHz)
- Memory bandwidth (GB/s)
- RAMDAC speed (MHz)
Step to optimize your perfomance
On This Page
| Clean up disk errors | |
| Remove temporary files | |
| Rearrange your data | |
| Make Internet Explorer run faster | |
| Automate Microsoft Update | |
| Install antivirus and antispyware programs |
Clean up disk errors
Run once a week
Whenever a program crashes, or you experience some power outage, your computer may create errors on your computer's hard disk. Over time, the errors can slow your computer. Luckily, the Windows operating system includes a Disk Check program to check and clean any errors on your computer and keep it running smoothly.
To run Disk Check:
1. | In your Start menu, click My Computer. |
2. | In the My Computer dialog box, right-click on the drive you wish to check for errors (for most of us this will be the C: drive, unless you have multiple drives on your computer), and click Properties. |
3. | In the Properties dialog box, click the Tools tab. In the Error-Checking section, press the Check Now… button. A Check Disk dialog box displays, as shown below.  Access Check Disk to check for errors on your computer. |
4. | In the Check Disk dialog box, check all the check boxes. Click Start. |
5. | You will see a message box that says you can schedule the disk check to start the next time you restart your computer. Click Yes. The next time you restart your computer, it will automatically run through a disk check before displaying your login screen. After the disk check finishes, Windows will automatically bring you to your login screen. Note: Check Disk can take more than an hour to check and clean errors on your computer. |
Remove temporary files
Run once a week
Your computer can pick up and store temporary files when you're looking at Web pages and even when you're working on files in programs, such as Microsoft Word. Over time, these files will slow your computer's performance. You can use the Windows Disk Cleanup screen to rid your computer of these deadbeat files.
To run Disk Cleanup:
1. | In your Start menu, click My Computer. |
2. | In the My Computer dialog box, right-click on the drive you wish to check for errors (for most of us this will be the C: drive, unless you have multiple drives on your computer), and click Properties. |
3. | In the Properties dialog box, click Disk Cleanup.  Use Disk Cleanup to help clear unused files from your computer. |
4. | Disk Cleanup will calculate how much space you can free up on your hard drive. After its scan, the Disk Cleanup dialog box reports a list of files you can remove from your computer, as pictured below. This scan can take a while depending on how many files you have lying around on your computer.  View results from the Disk Cleanup dialog box. |
5. | After the scan is complete, in the Disk Cleanup dialog box, click View Files to see what Disk Cleanup will throw out once you give it the go ahead. You can check and uncheck boxes to define what you wish to keep or discard. When you're ready, click OK. |
6. | You can also select the More Options tab within the Disk Cleanup screen to look for software programs you don't use much anymore. You then have the choice to remove these unused programs. |
Rearrange your data
Run once a month
Don't be shocked, but your computer can get sloppy. Your computer often breaks files side by side to increase the speed of access and retrieval. However, as files are updated, your computer saves these updates on the largest space available on the hard drive, often found far away from the other adjacent sectors of the file.
The result: a fragmented file. Fragmented files cause slower performance. This is because your computer must now search for all of the file's parts. In other words, your computer knows where all the pieces are, but putting them back together, and in the correct order when you need them, can slow your computer down.
Windows includes a Disk Defragmenter program to piece all your files back together again (if only Humpty-Dumpty had been so lucky) and make them quicker to open.
To run the Disk Defragmenter:
1. | In your Start menu, click My Computer. |
2. | In the My Computer dialog box, right-click on the drive you wish to check for errors (for most of us this will be the C: drive, unless you have multiple drives on your computer), and click Properties. |
3. | In the Properties dialog box, click the Tools tab, and then in the Defragmentation section, click Defragment Now…. |
4. | In the Disk Defragmenter dialog box, select the Volume (most likely your Local Disk C:) at the top of the screen, and then click Analyze. |
5. | After analyzing your computer, the Disk Defragmenter displays a message stating whether you should defragment your computer. Press Defragment to clean up your computer if necessary. The Disk Defragmenter will reorganize files by placing together and organizing them by program and size, as shown in Figure 5.  Files being reorganizing with the Disk Defragmenter. |
Make Internet Explorer run faster
The Web is a sparkling achievement of modern society. It's everywhere—from the home to the classroom. We use it to communicate, to work, to play—even to waste time when there's nothing else to do.
Yet there's nothing more frustrating than having this technical marvel at our fingertips 24 hours a day, 7 days a week, only to watch our computers access the Internet at a crawling pace. Thankfully, Microsoft Internet Explorer provides some useful options for quicker Web surfing. Let's look at these options now.
Reduce the size of your Web page history
Internet Explorer stores visited Web pages to your computer, organizing them within a page history by day. While it's useful to keep a couple days of Web history within your computer, there's no need to store more than a week's worth. Any more than that and you're collecting Web pages that will slow down your computer's performance.
To reduce your Web page history:
1. | In Internet Explorer, on the Tools menu, click Internet Options. |
2. | In the Internet Options dialog box, in the History section, find the Days to keep pages in history: box. Type "1" in this box, as pictured in the image below. Click OK.  Reduce the number of days to keep pages in history. |
Don't save encrypted Web pages
Encrypted Web pages ask for usernames and passwords. These pages scramble information to prevent the reading of this sensitive information. You can define Internet Explorer to not save these types of pages. You'll free up space by saving fewer files to your computer, as well as keeping secure information off your computer.
To not save encrypted Web pages:
1. | In Internet Explorer, on the Tools menu, click Internet Options. |
2. | In the Internet Options dialog box, click the Advanced tab. |
3. | In the Settings section, scroll down to the Security section. Check the "Do not save encrypted pages to disk" option, as shown in the figure below. Click OK.  Set up Internet Explorer so that you do not save encrypted Web pages. |
Automate Microsoft Update
Configure once
Microsoft works constantly to release updates to Windows and other Microsoft products, including Office. At Microsoft Update, you can find and install all these updates—not just the critical ones. Often, these updates will improve your computer's performance.
You can make life easier by automating Microsoft Update so your computer downloads and installs all the updates without you having to worry about them.
To automate Microsoft Update:
1. | In your Start menu, click Control Panel. |
2. | In the Automatic Updates dialog box, check the Automatic (Recommended) check box. You can define the time of day when your computer checks for updates. If the computer finds any updates, it will download and install them automatically for you. |
3. | Click OK.  Automate Microsoft Update to keep your computer up to date. |
Install antivirus and antispyware programs
Computer viruses and spyware (hidden software that gathers information about you without your knowledge or consent when you're using a computer) both reduce system performance. Computer viruses can not only reduce performance, but they can also destroy data. Any computer that accesses the Internet should have antivirus and antispyware programs installed.
Antivirus programs: Two of the most reliable computer virus programs around are Norton Internet Security and McAfee Internet Security Suite. Find additional antivirus programs on Windows Marketplace. | |
Antispyware programs: For a great antispyware program, check out Windows Defender. |
Smooth running
Follow these steps and you'll have your computer purring like a vintage Porsche (or whatever your dream car of choice is). And the best part—maintaining your computer is a lot less messy than an automobile. You don't even have to roll up your sleeves.
Article source from http://www.microsoft.com/athome/moredone/optimize.mspx#EKB
written by Chris Tull

